Host & Network Penetration Testing: Post-Exploitation
Post-exploitation is the final phase of the penetration testing process and consists of the tactics, techniques and procedures that attackers/adversaries undertake after obtaining initial access on a target system. In this course, you will learn about how to perform local enumeration on target systems to identify critical information like the users and groups, credentials and services. You will also learn how to elevate your privileges on Windows and Linux targets, as well as how to maintain access to target systems after compromise.
You will also learn how to dump and crack hashes for the purpose of legitimate authentication or lateral movement.
Furthermore, you will also learn how to perform internal network discovery and how to pivot to systems you have discovered on the target’s internal network.
The objective of this course is to give you in-depth hands-on skills necessary to perform all the tasks that make up the post-exploitation phase of the penetration testing lifecycle.
主机与网络渗透测试:后渗透阶段
后渗透是渗透测试过程的最后阶段,包括攻击者在获得目标系统初始访问权限后采取的策略、技术和程序。在本课程中,您将学习如何对目标系统进行本地枚举,以识别关键信息,如用户和组、凭据和服务。您还将学习如何提升在Windows和Linux目标系统上的权限,以及如何在受损后保持对目标系统的访问。
您还将学习如何转储和破解哈希,以进行合法身份验证或横向移动。
此外,您还将学习如何进行内部网络发现,并如何转移到在目标内部网络上发现的系统。
本课程的目标是为您提供深入的实践技能,以执行渗透测试生命周期中后渗透阶段的所有任务。
Course Introduction
Course Topic Overview
- Introduction to Post-Exploitation
- Windows Local Enumeration
- Linux Local Enumeration
- Transferring Files To Windows & Linux Targets
- Upgrading Shells
- Windows Privilege Escalation
- Linux Privilege Escalation
- Windows Persistence
- Linux Persistence
- Dumping & Cracking Windows Hashes
- Dumping & Cracking Linux Hashes
- Pivoting
- Clearing Your Tracks
课程介绍
课程主题概述
- 后渗透简介
- Windows 本地枚举
- Linux 本地枚举
- 将文件传输到 Windows 和 Linux 目标系统
- 升级 Shell
- Windows 权限提升
- Linux 权限提升
- Windows 持久化
- Linux 持久化
- 转储和破解 Windows 哈希
- 转储和破解 Linux 哈希
- 枢纽转移
- 清除痕迹
Prerequisites
- Basic familiarity with TCP & UDP
- Basic familiarity with Linux & Windows
- Basic familiarity with Metasploit
先决条件
- 对TCP和UDP的基本了解
- 对Linux和Windows的基本了解
- 对Metasploit的基本了解
Learning Objectives
- Students will get an introduction to the post-exploitation phase of a penetration test.
- Students will learn how to perform and automate local enumeration on Windows & Linux systems.
- Students will learn how to transfer files to Windows & Linux targets.
- Students will get an understanding of how to updrade shells.
- Students will learn how to elevate privileges on both Windows & Linux systems.
- Students will learn how to establish persistence on both Windows & Linux systems.
- Students will learn how to dump & crack Windows & Linux user account hashes.
- Students will learn how to pivot onto other systems on the target network.
- Students will leanr how to clear their tracks on both Windows & Linux targets.
学习目标
- 学生将了解渗透测试中后渗透阶段的概述。
- 学生将学习如何在Windows和Linux系统上执行和自动化本地枚举。
- 学生将学习如何将文件传输到Windows和Linux目标系统。
- 学生将了解如何升级Shell。
- 学生将学习如何在Windows和Linux系统上提升权限。
- 学生将学习如何在Windows和Linux系统上建立持久性。
- 学生将学习如何转储和破解Windows和Linux用户帐户哈希。
- 学生将学习如何在目标网络上转移到其他系统。
- 学生将学习如何清除在Windows和Linux目标系统上的痕迹。
Introduction To Post-Exploitation
Post-Exploitation
Post-exploitation is the final phase of the penetration testing process and consists of the tactics, techniques and procedures that attackers/adversaries undertake after obtaining initial access on a target system.
In other words, post-exploitation involves what you do or have to do once you gain an initial foothold on the target system.
Post-exploitation will differ based on the target operating system as well as the target infrastructure.
后渗透简介
后渗透
后渗透是渗透测试过程的最后阶段,包括攻击者在获得目标系统初始访问权限后采取的策略、技术和程序。
换句话说,后渗透涉及在获得目标系统的初始立足点后所需做或必须做的事情。
后渗透的具体内容将根据目标操作系统以及目标基础设施而有所不同。
Post-Exploitation
The post-exploitation techniques and tools that you can use will depend on what kind of access you have on the system you have compromised as well as how stealthy you have to be.
This ultimately means that you will need to utilize different techniques and tools based on the target operating system and its configuration.
The post-exploitation techniques you can run against the target will need to abide by the rules of engagement agreed upon with the client you are performing the pentest for.
Note: When running post-exploitation techniques, you need to be sure that you have the necessary permissions and rights to modify services, system configurations, perform privilege escalation, delete logs etc.
后渗透
您可以使用的后渗透技术和工具将取决于您在已被攻破的系统上拥有何种访问权限,以及您需要保持多么隐秘。
这意味着您需要根据目标操作系统及其配置来使用不同的技术和工具。
您可以对目标运行的后渗透技术需要遵守与您进行渗透测试的客户达成的规定的参与规则。
注意:在运行后渗透技术时,您需要确保拥有必要的权限和权利来修改服务、系统配置、执行权限提升、删除日志等操作。
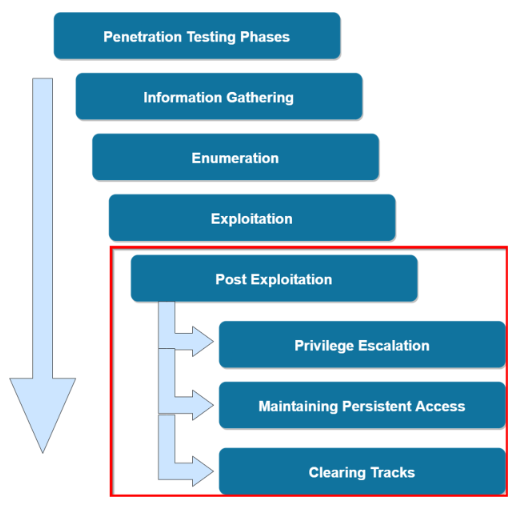
Post-Exploitation
This diagram outlines the various phases of the penetration testing lifecycle and highlights the post exploitation phase and the techniques that fall under the post-exploitation phase.
Penetration Testing Phases
- Information Gathering
- Enumeration
- Exploitation
- Post Exploitation
- Privilege Escalation
- Maintaining Persistent Access
- Clear Tracks
后渗透
这张图解说明了渗透测试生命周期的各个阶段,并突出了后渗透阶段以及属于后渗透阶段的技术。
渗透测试阶段
- 信息收集
- 枚举
- 利用
- 后渗透
- 权限提升
- 保持持久访问
- 清除痕迹
Post-Exploitation Methodology
Post-Exploitation Methodology
In order to perform a thorough and complete post-exploitation phase, we need to utilize a structured methodology that encompasses the most important stages of post-exploitation that can be applied during engagements.
This structured, methodological approach ensures that we do not skip/overlook important phases of the post-exploitation phase in addition to providing us with trackable objectives based on each stage.
渗透后阶段方法论
渗透后阶段方法论
为了进行彻底和完整的渗透后阶段,我们需要采用一种结构化的方法论,包括在合作中可以应用的最重要的渗透后阶段。
这种结构化的方法论确保我们不会跳过/忽视渗透后阶段的重要阶段,同时为我们提供基于每个阶段的可追踪的目标。
Post-Exploitation Methodology
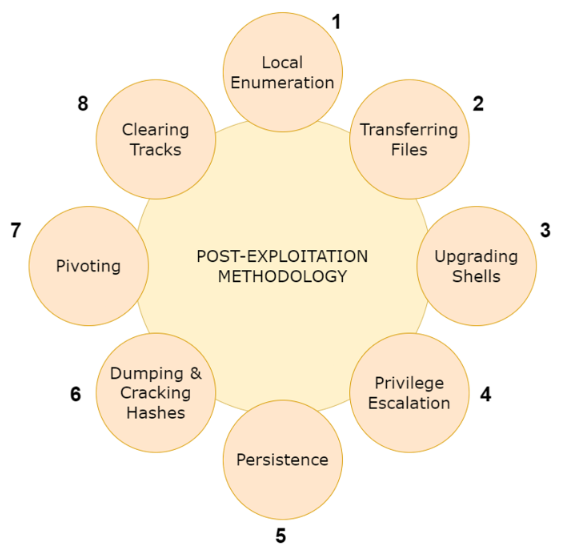
POST-EXPLOITATION METHODOLOGY
- Local Enumeration
- Transferring Files
- Upgrading Shells
- Privilege Escalation
- Persistence
- Dumping & Cracking Hashes
- Pivoting
- Clearing Tracks
渗透后阶段方法论
- 本地枚举
- 文件传输
- 升级 Shell
- 权限提升
- 持久性
- 密码哈希破解与转储
- 转向攻击
- 清除痕迹
Post-Exploitation Methodology
- Local Enumeration
- Enumerating System Information
- Enumerating Users And Groups
- Enumerating Network Information
- Enumerating Services
- Automating Local Enumeration
- Transferring Files
- Setting Up A Web Server With Python
- Transferring Files To Windows Targets
- Transferring Files To Linux Targets
- Upgrading Shells
- Upgrading Command Shells To Meterpreter
- Spawning TTY Shells
- Privilege Escalation
- Identify PrivEsc Vulns
- Windows PrivEsc
- Linux PriEsc
- Persistence
- Setting Up Persistence On Windows
- Setting Up Persistence On Linux
- Dumping & Cracking Hashes
- Dumping & Cracking Windows Hashes
- Dumping & Cracking Linux Hashes
- Pivoting
- Internal Network Recon
- Pivoting
- Clearing Your Tracks
- Clearing your Tracks On Windows & Linux
渗透后阶段方法论
- 本地枚举
- 枚举系统信息
- 枚举用户和组
- 枚举网络信息
- 枚举服务
- 自动化本地枚举
- 文件传输
- 使用 Python 设置 Web 服务器
- 将文件传输到 Windows 目标
- 将文件传输到 Linux 目标
- 升级 Shell
- 将命令 Shell 升级为 Meterpreter
- 生成 TTY Shell
- 权限提升
- 识别提权漏洞
- Windows 提权
- Linux 提权
- 持久性
- 在 Windows 上设置持久性
- 在 Linux 上设置持久性
- 转储与破解哈希
- 转储与破解 Windows 哈希
- 转储与破解 Linux 哈希
- 转向攻击
- 内部网络侦查
- 转向攻击
- 清除痕迹
- 清除痕迹(Windows 和 Linux)