Linux Black Box Penetration Test
Penetration Testing Phases
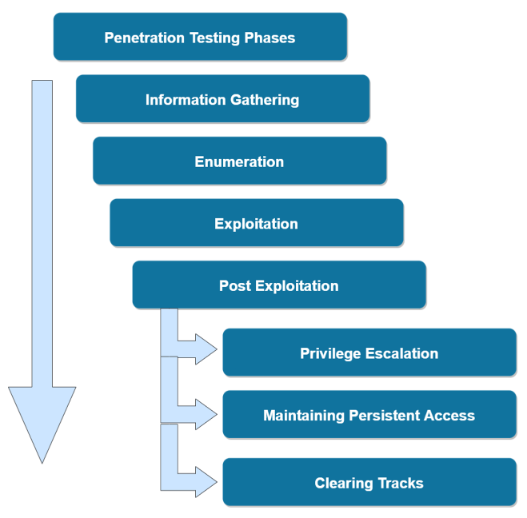
The following diagram outlines the various phases involved in a typical penetration test.
Black Box Methodology:
- Host discovery
- Port scanning & enumeration
- Vulnerability detection/scanning
- Exploitation
- Manual
- Automated
- Post Exploitation
- Privilege Escalation
- Persistence
- Dumping Hashes
Penetration Testing Phases
- Information Gathering
- Enumeration
- Exploitation
- Post Exploitation
- Privilege Escalation
- Maintaining Persistent Access
- Clearing Tracks
渗透测试阶段
下图概述了典型渗透测试中涉及的各个阶段。

黑盒方法论:
- 主机发现
- 端口扫描和枚举
- 漏洞检测/扫描
- 利用
- 手动
- 自动化
- 后期利用
- 提权
- 持久化
- 转储哈希
渗透测试阶段
- 信息收集
- 枚举
- 利用
- 后期利用
- 提权
- 保持持久访问
- 清理痕迹
Scenario & Scope
You have just begun your first job as a Junior Penetration Tester and have been assigned to assist in performing a penetration test on client’s network.
The pentest lead was pleased with your ability to gain access to the Windows Server target and has assigned you to perform a pentest on a Linux server on the client’s network.
Your primary objectives are:
- Identify services running on the target.
- Identify vulnerabilities within the services.
- Exploit these vulnerabilities to obtain an initial foothold.
Note: You are permitted to use the Metasploit Framework.
场景和范围
您刚刚开始第一份初级渗透测试员的工作,并被指派协助在客户的网络上执行渗透测试。
渗透测试负责人对您能够访问 Windows Server 目标的能力感到满意,并已指派您在客户端网络上的 Linux 服务器上执行渗透测试。
您的主要目标是:
- 识别在目标上运行的服务。
- 识别服务中的漏洞。
- 利用这些漏洞获得初步的立足点。
注意:您被允许使用 Metasploit 框架。