Host & Network Penetration Testing: Exploitation
Exploitation consists of the tactics, techniques and procedures that attackers/adversaries utilize in order to gain an initial foothold on a target system and consequently the target network. The ability to identify and exploit vulnerabilities is an important skill to master on your journey to becoming a skilled penetration tester. In this course, you will learn about how to identify vulnerabilities on a target by performing banner grabbing and vulnerability detection. In addition to identifying vulnerabilities, you will also learn how to search for and modify exploit code that will be used to exploit a particular vulnerability on a target system.
Furthermore, this course will also introduce you to bind and reverse shells and will demonstrate how they work and how they can be used to gain remote access to a Windows or Linux target.
After identifying vulnerabilities on a target system, you will learn how to exploit these vulnerabilities both manually and automatically through the use of exploitation frameworks like Metasploit and PowerShell-Empire.
This course also covers the process of encoding and obfuscating exploits and payloads in order to avoid detection by signature based AV’s.
The objective of this course is to give you in-depth hands-on skills necessary to identify and exploit vulnerabilities on a target system both manually and automatically.
主机和网络渗透测试:利用
利用包括攻击者/对手为了在目标系统上获得初始立足点并最终在目标网络上获得初始立足点而使用的策略、技术和程序。 识别和利用漏洞的能力是成为一名熟练的渗透测试人员的重要技能。 在本课程中,您将学习如何通过执行横幅抓取和漏洞检测来识别目标上的漏洞。 除了识别漏洞之外,您还将学习如何搜索和修改将用于利用目标系统上特定漏洞的利用代码。
此外,本课程还将向您介绍绑定和反向 shell,并将演示它们的工作原理以及如何使用它们获得对 Windows 或 Linux 目标的远程访问。
在识别目标系统上的漏洞后,您将学习如何通过使用 Metasploit 和 PowerShell-Empire 等利用框架手动和自动利用这些漏洞。
本课程还涵盖了编码和混淆漏洞利用和有效载荷的过程,以避免被基于签名的 AV 检测到。
本课程的目的是为您提供手动和自动识别和利用目标系统漏洞所需的深入实践技能。
Introduction To Exploitation
Course Topic Overview
- Introduction To Exploitation
- Vulnerability Scanning
- Searching For Exploits
- Fixing Exploits
- Bind & Reverse Shells
- Exploitation Frameworks
- Windows Exploitation
- Linux Exploitation
- AV Evasion & Obfuscation
利用简介
课程主题概述
- 利用简介
- 漏洞扫描
- 寻找漏洞
- 修复漏洞
- 绑定和反向 Shell
- 利用框架
- Windows利用
- Linux利用
- AV 规避和混淆
Prerequisites
- Basic familiarity with TCP & UDP
- Basic familiarity with Linux & Windows
- Basic familiarity with Metasploit
先决条件
- 基本熟悉 TCP 和 UDP
- 基本熟悉 Linux 和 Windows
- 基本熟悉 Metasploit
Learning Objectives
Students will get an introduction to the exploitation phase of a penetration test.
Students will learn how to identify vulnerable services running on a target system.
Students will learn how to search for, modify and compile publicly available exploit code.
Students will get an understanding of how bind and reverse shells work.
Students will get an understanding of the various exploitation frameworks available as well as how they can be used to streamline exploitation.
Students will learn how to exploit both Windows & Linux systems in a simulated black box penetration test.
Students will learn how to evade signature based AV solutions.
学习目标
学生将了解渗透测试的利用阶段。
学生将学习如何识别目标系统上运行的易受攻击的服务。
学生将学习如何搜索、修改和编译公开可用的漏洞利用代码。
学生将了解绑定和反向 shell 的工作原理。
学生将了解可用的各种利用框架以及如何使用它们来简化利用。
学生将学习如何在模拟黑盒渗透测试中同时利用 Windows 和 Linux 系统。
学生将学习如何规避基于签名的 AV 解决方案。
Introduction To Exploitation
Exploitation
Exploitation consists of techniques and tools used by adversaries/penetration testers to gain an initial foothold on a target system or network.
Successful exploitation will heavily depend on the nature and quality of information gathering and service enumeration performed on the target.
- We can only exploit a target if we know what is vulnerable - Unknown
So far, we have covered exploitation of Windows & Linux systems both manually and automatically, however, we still need to get a clearer picture of the exploitation methodology and the tools and techniques involved in the process.
利用简介
利用
利用包括对手/渗透测试人员用来在目标系统或网络上获得初始立足点的技术和工具。
成功利用将在很大程度上取决于对目标执行的信息收集和服务枚举的性质和质量。
- 如果我们知道什么是易受攻击的,我们只能利用目标 - 未知
到目前为止,我们已经介绍了手动和自动利用 Windows 和 Linux 系统,但是,我们仍然需要更清楚地了解利用方法以及该过程中涉及的工具和技术。
Penetration Testing Execution Standard
The Penetration Testing Execution Standard (PTES) is a penetration testing methodology that was developed by a team of information security practitioners with the aim of addressing the need for a comprehensive and up-to-date standard for penetration testing.
渗透测试执行标准
渗透测试执行标准 (PTES) 是一种渗透测试方法,由信息安全从业人员团队开发,旨在满足对全面和最新的渗透测试标准的需求。
Penetration Testing Phases
The following diagram outlines the various phases involved in a typical penetration test.
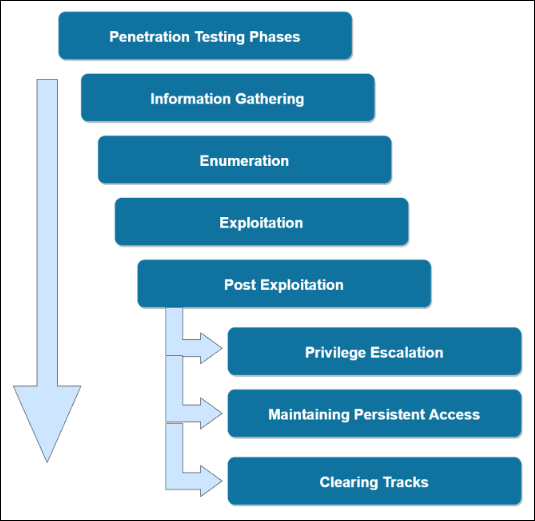
Penetration Testing Phases
- Information Gathering
- Enumeration
- Exploitation
- Post Exploitation
- Privilege Escalation
- Maintaining Persistent Access
- Clearing Tracks
Exploitation Methodology:
- Identify Vulnerable Services
- Identify & Prepare Exploit Code
- Gaining Access
- Automated - MSF
- Manual
- Obtain remote access on target system
- Bypass AV detection
- Pivot on to other systems
渗透测试阶段
下图概述了典型渗透测试中涉及的各个阶段。

渗透测试阶段
- 信息收集
- 枚举
- 利用
- 后期利用
- 特权升级
- 维护持久访问
- 清除痕迹
利用方法:
- 识别易受攻击的服务
- 识别和准备利用代码
- 获得访问权限
- 自动化 - MSF
- 手动的
- 获得对目标系统的远程访问
- 绕过 AV 检测
- 转向其他系统